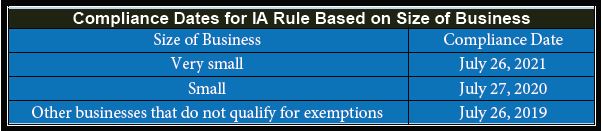
While much of the attention of late has been focused on the Produce Safety Rule for farms and hullers, and the Preventive Controls Rule for Human Food for processors, there is another rule that tree nut processors must be gearing up for and implementing. Why? Because inspections were slated to start happening in March 2020. The FDA Food Safety Modernization Act (FSMA) final rule for Intentional Adulteration (IA) is aimed at preventing intentional adulteration from acts intended to cause wide-scale harm to public health, including acts of terrorism targeting the food supply. Such acts, while not likely to occur, could cause illness, death, and/or economic disruption of the food supply absent mitigation strategies. Rather than targeting specific foods or hazards, this rule requires mitigation (risk-reducing) strategies for processes in certain registered food facilities.
While acts of intentional adulteration may take many forms, including acts of disgruntled employees or economically motivated adulteration, the goal of this rule is to prevent acts intended to cause wide-scale harm. It is designed to primarily cover large companies whose products reach many people, exempting smaller companies. It does not cover farms.
For the IA rule, FDA has taken an approach similar to Hazard Analysis Critical Control Point (HACCP) system, an approach adopted by industry for the identification, evaluation and control of food safety hazards. Each covered facility is required to prepare and implement a food defense plan. This written plan must identify vulnerabilities and actionable process steps, mitigation strategies, and procedures for food defense monitoring, corrective actions and verification. A “reanalysis” is required every three years or when certain criteria are met, including mitigation strategies that are determined to be improperly implemented.
Each facility subject to the rule must conduct a vulnerability assessment. This is the identification of vulnerabilities and actionable process steps for each type of food manufactured, processed, packed or held at the food facility. For each point, step, or procedure in the facility’s process, the following elements must be evaluated:
-
- The severity and scale of the potential impact on public health. This would include such considerations as the volume of product, the number of servings, the number of exposures, how fast the food moves through the distribution system, potential agents of concern and the infectious/lethal dose of each; and the possible number of illnesses and deaths.
- The degree of physical access to the product. Things to be considered would include the presence of such physical barriers as gates, railings, doors, lids, seals and shields.
- The ability to successfully contaminate the product.
Mitigation Strategies: These should be identified and implemented at each actionable process step to provide assurances that vulnerabilities will be minimized or prevented. The mitigation strategies must be tailored to the facility and its procedures. To help facilities with this effort, the FDA has created the “Food Defense Mitigation Strategies Database (FDMSD).” The FDMSD is a tool designed to help owners and operators of a food facility identify mitigation strategies to protect against intentional adulteration. It contains a collection of potential mitigation strategies that could be implemented to significantly minimize or prevent vulnerabilities at actionable process steps, and is intended as a starting point for facilities to consider when identifying potential mitigation strategies. Facilities can customize and tailor strategies listed in the FDMSD to apply to their specific circumstances. The FDMSD is not an exhaustive list of potential mitigation strategies, and facilities can create their own.
Mitigation Strategy Management Components
Steps must be taken to ensure the proper implementation of each mitigation strategy. In each of these areas of food defense, the facilities are given flexibility to establish the actions most appropriate to their operation and product.
Monitoring: Establishing and implementing procedures, including the frequency with which they are to be performed, for monitoring the mitigation strategies.
Corrective actions: You must establish and implement written food defense corrective actions procedures that must be taken if mitigation strategies are not properly implemented. The procedures must describe the corrective actions steps you would take to ensure that appropriate action is taken to identify and correct a problem that has occurred with implementation of a mitigation strategy and, when necessary, to reduce the likelihood that the problem will recur. Corrective actions must be appropriate to the nature of the actionable process step and the nature of the mitigation strategy. It must also be documented.
Verification: Verification activities would ensure that monitoring is being conducted and appropriate decisions about corrective actions are being made. Verification is the application of methods, procedures, and other evaluations to determine whether a mitigation strategy or combination of mitigation strategies is or has been operating as intended according to the food defense plan. Food defense verification activities must be documented: Verification that food defense monitoring is being conducted; Verification that appropriate decisions about food defense corrective actions are being made; Verification that mitigation strategies are properly implemented and are significantly minimizing or preventing the significant vulnerabilities. To do so, you must conduct activities that include all of the following:
-
- Review of the food defense monitoring and food defense corrective actions records to ensure that the records are complete, the activities reflected in the records occurred in accordance with the FDP, the mitigation strategies are properly implemented, and appropriate decisions were made about food defense corrective actions.
- Other activities appropriate for verification of proper implementation of mitigation strategies.
- Verification of reanalysis.
Training and recordkeeping: Facilities must ensure that personnel assigned to the vulnerable areas receive appropriate training; facilities must maintain records for food defense monitoring, corrective actions, and verification activities.
You are required to make and keep records related to the following:
-
- Food defense plan, including vulnerability assessment, mitigation strategies, monitoring procedures, corrective actions procedures, and verification procedures
- Documentation of food defense monitoring of mitigation strategies
- Documentation of food defense corrective actions taken
- Documentation of food defense verification activities
- Documentation of food defense plan reanalysis
- Records documenting required training
If you haven’t started putting together your food defense plan, and addressing the potential for intentional adulteration, now is the time. One useful tool is FDA’s Food Defense Plan Builder, which can be found online at http://www.fda.gov/food/food-defense-tools-educational-materials/food-defense-plan-builder. They just released Version 2.0, and it is pretty handy. The time has come for tree nut facilities to have their food defense plans in place and operational. An IA rule inspection could be just around the corner.

Roger A. Isom
Roger is President/CEO of the California Cotton Ginners and Growers Association and Western Tree Nut Association. He brings over 30 years of regulatory and legislative advocacy experience, specializing in environmental and safety matters. Roger’s responsibilities include the management of both Associations’ staff and day-to-day operations. Roger is also the President of the Ag Energy Consumers Association (AECA), board member and Past President of the Ag One Foundation at California State University Fresno, and manages the Navel Orangeworm Action Committee (NOWAC).